How to Defend Your Website with Zip Bombs
If you have ever hosted a website or even administrated a server, you'll be very well aware of bad people trying bad things with your stuff.
When I first hosted my own little linux box with SSH access at age 13, I read through the logs daily and reported the IPs (mostly from China and Russia) who tried to connect to my sweet little box (which was actually an old ThinkPad T21 with a broken display running under my bed) to their ISPs.
Actually, if you have a linux server with SSH exposed you can see how many connection attempts are made every day:
grep 'authentication failures' /var/log/auth.log
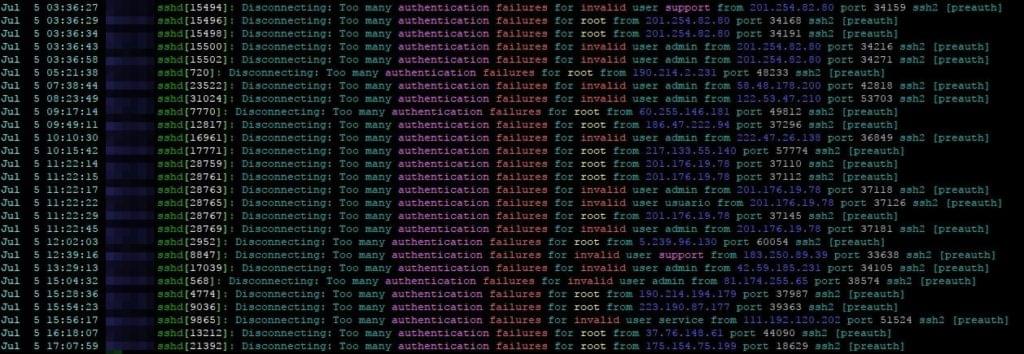
Wordpress has doomed us all
OK, to be honest, web vulnerability scanners have existed before Wordpress, but since WP is so widely deployed most web vulnerability scanners include scans for some misconfigured wp-admin folders or unpatched plugins.
So if a small, new hacking group wants to gain some hot cred they'll download one of these scanner things and start testing against many websites in hopes of gaining access to a site and defacing it.
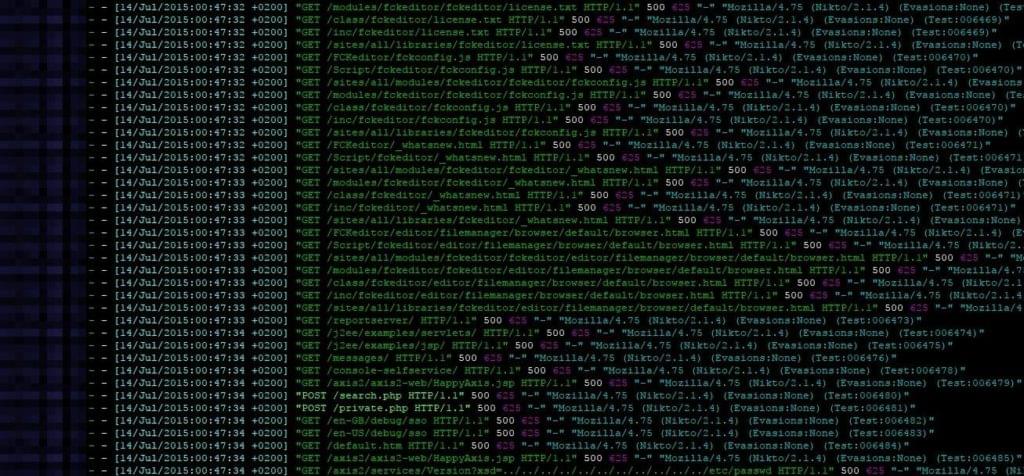
This is why all server or website admins have to deal with gigabytes of logs full with scanning attempts. So I was wondering..
Is there a way to strike back?
After going through some potential implementations with IDS or Fail2ban I remembered the ZIP bombs from the old days.
Continue reading %How to Defend Your Website with Zip Bombs%